How to Detect Keyloggers in Windows Systems
Keyloggers are a dangerous security threat which can easily target even up-to-date computers. Their aim is to monitor your keystrokes and expose that private data to hackers and surveillance agents. While you may use anti-keylogger software, it’s far more effective to detect these threats in advance before they do any serious damage.
Here are some of the best ways to detect keyloggers in a Windows computer. We will also discuss an advanced preventative technique called “keystroke encryption” that neutralizes even the most sophisticated keyloggers.
What are Keyloggers?
A keylogger is a piece of software or hardware which monitors the keystrokes entered on a computer/laptop keyboard or mobile device. Hardware keyloggers are inserted using USB or a rogue driver and are easier to detect and remove. The software keyloggers are stealthier in comparison and are sometimes undetectable in the infected system.
Unlike regular viruses and Trojans, remote keyloggers do not impact the system performance but do a lot more harm by exposing your private information to others. Think of financial information, passwords, and your anonymous online posts and comments.

The most sophisticated of these surveillance agents can profile users based on keystroke analysis, the rhythm and pattern of their keystroke entries. If that very idea scares you, take solace in the fact that for any keylogger to be effective, it has to first install properly in your computer. There are various categories of keyloggers, depending on the severity.
- Browser-based keyloggers: some malicious websites may use CSS scripts, Man-In-the-Browser (MITB) attacks, or web form-based keyloggers. Fortunately, if you have an updated Windows 10 system and have enabled Windows Defender and other essentials of Windows security, these threats will be blocked immediately.
- General Spyware keyloggers: traditional keyloggers are inserted using a suspicious email attachment or a social media/torrent download. Again, they are likely to be blocked by Windows Defender or an anti-malware program.
- Kernel-level keyloggers: these are more dangerous. They operate underneath the Windows operating system as rootkits, and can go undetected.
- Hypervisor-based keyloggers: using virtualization, the sophisticated keyloggers can establish themselves as replicas of the operating system, and scan all keystrokes. These threats are very rare though.
If you suspect that your Windows system has been attacked by keyloggers, follow these steps to ensure your data is safe.
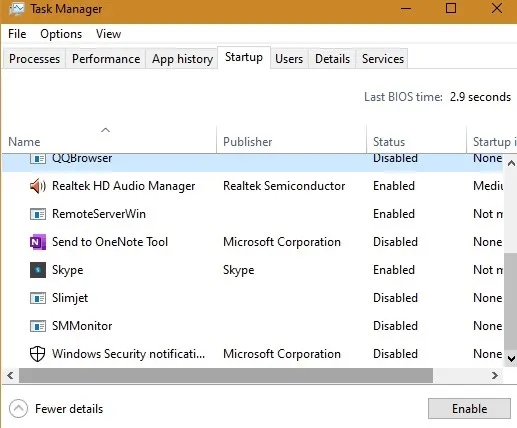
Use the Task Manager to Detect Keyloggers

Also, check under the “Startup” tab. If there are any suspicious-looking programs in the boot menu, disable them.
Detect Suspicious Internet Connections Using Command Line
Once you’ve ensured that no one else is logged in on your computer, it’s important to check whether there are any suspicious Internet connections to your device. To do this, open Windows command line in Administrator mode and enter the following:
netstat -b

All the websites and software connected online to your Windows computer are now visible. The ones connected to Windows Store, Edge browser, or other system apps such as “svchost.exe” are harmless. Check the IP addresses online for any possible remote location.
Use Anti-Rootkit Malware Solutions
If you think you are the victim of a kernel-level keylogger, you need to use an effective anti-rootkit malware solution.
Among the lightweight solutions, McAfee has a free rootkit removal tool. As soon as you install it, it will check for updates and kernel-mode threats including rootkit keyloggers. The process is very fast and reliable, and this rootkit removal tool does not cause any burden on your Windows system.
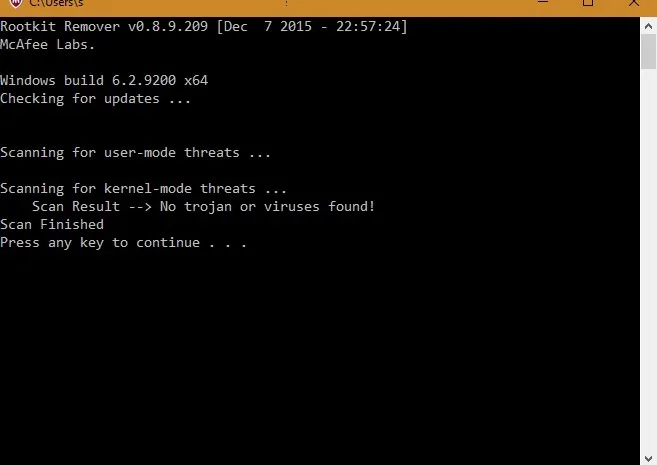
Currently there are no effective means to detect hypervisor-level keyloggers as such a virtual system can remain invisible, and go undetected by you. However, if you suspect that you’re the victim of such an attack by Big Brother, there’s one technique that you can prevent your keyboard from sending them your data.
Advanced Technique: Keystroke Encryption
Keystroke encryption is a fantastic way to prevent keylogging by encrypting all your keystrokes before they are sent online. If you are the victim of a hypervisor-level keylogger attack, the malware will only be able to detect encrypted random characters.
KeyScrambler is one of the popular keystroke encryption solution. It is virus-free and safe to use with over one million paid users. The software’s Personal edition is free and can secure keystroke data across 60+ browsers. The software can be downloaded from its official website.
After installation, you can enable KeyScrambler from the right system tray.

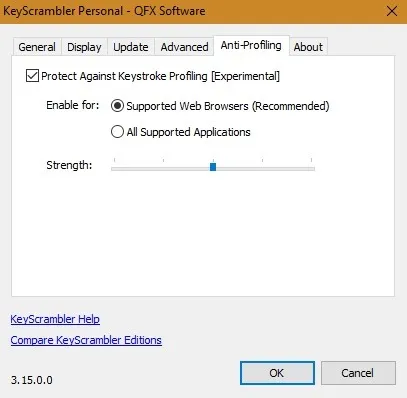
In the Settings, you can protect against keystroke profiling. It is done using a feature that moderates your typing rhythm to protect your anonymity against websites that attempt to profile you by the way you type.
As soon as you enter keystrokes in any browser such as Google Chrome or Firefox, KeyScrambler will encrypt all your keystrokes which you can see LIVE on your screen.

Despite the serious threat it poses, protecting yourself from keylogging is not that difficult. You can ramp up your defenses using Windows Defender. There are a few warning signs: if your system is much slower than usual, or you start noticing unwanted pop-ups and advertisements, or there is a change in browser settings or the search engine used, your system may have been compromised. You can use the techniques discussed above to get to the heart of the problem.
Do you suspect that you may be a victim of keyloggers? Please share with us why it appears that way to you.
Image Credit: Robert van der Steeg
- Tweet
Leave a Reply