How to Block Ads with Pi Hole
A Pi-Hole is a network-wide ad blocker that intercepts ads on any device on your network. It targets a list of thousands of ad-serving domains and directs their content to a black hole, removing them from sight. It can work any any device that’s connected to your network, without additional software. It even runs in mobile device apps, reducing bandwidth usage and improving performance. This tutorial shows how to run Pi Hole on your Linux machine.
What Is Pi-Hole?
Pi-Hole calls itself “a black hole for Internet advertisements.” It works by running all outbound server requests against an internal blocklist. To make this happen, you’ll need to set the Pi-Hole as your DNS server. This allows it to handle address resolution requests and view the IP addresses of requested information. As a result, it has the power to selectively mute certain outbound requests based on their IP addresses.
If the Pi-Hole sees a connection request that matches its blocklist, it blocks that request from reaching the ad server or destination. Over 10,000 domains are on the blocklist, and it stops requests from ever reaching their servers. No ads are downloaded, so bandwidth is saved and connection speed is improved.
Pi-Hole doesn’t just block ads, either. It can also protect your network against all kinds of Web-based attack vectors. The system also includes a robust web-based portal for monitoring and auditing Pi-Hole’s operation.
Better still, all of this is free and open source. The only part that isn’t open source is the name and logo, which are registered as trademarks.
Installing Pi-Hole
While Pi-Hole can run on just about any Linux-capable device, the developers of the program officially support these distros:
- Raspbian: Buster / Bullseye
- Ubuntu: 20.04 / 22.04 / 22.10
- Fedora: 36 / 37
- Debian: 10 / 11
- CentOS Stream: 8 / 9
Follow the steps below to install Pi-Hole on an Ubuntu 22.10 desktop machine.
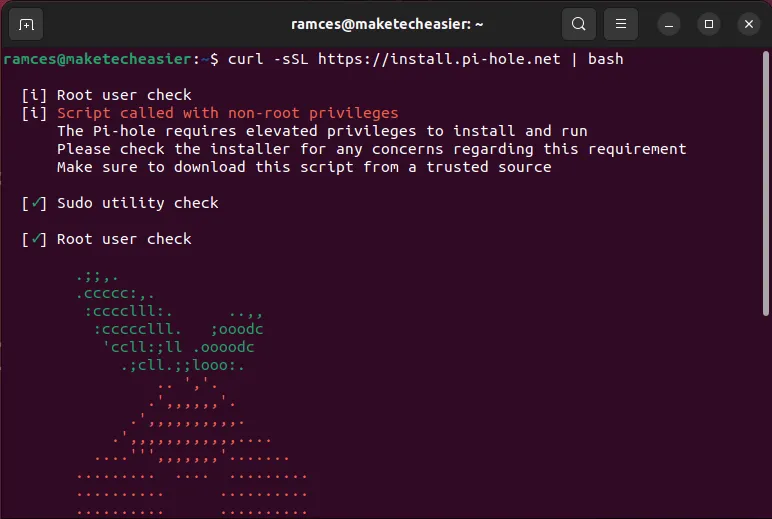
- Open a Terminal and run the command below to install the software:
curl -sSL https://install.pi-hole.net | bash
- After the installation, set the Pi-Hole as your DNS server in your router’s configuration page.
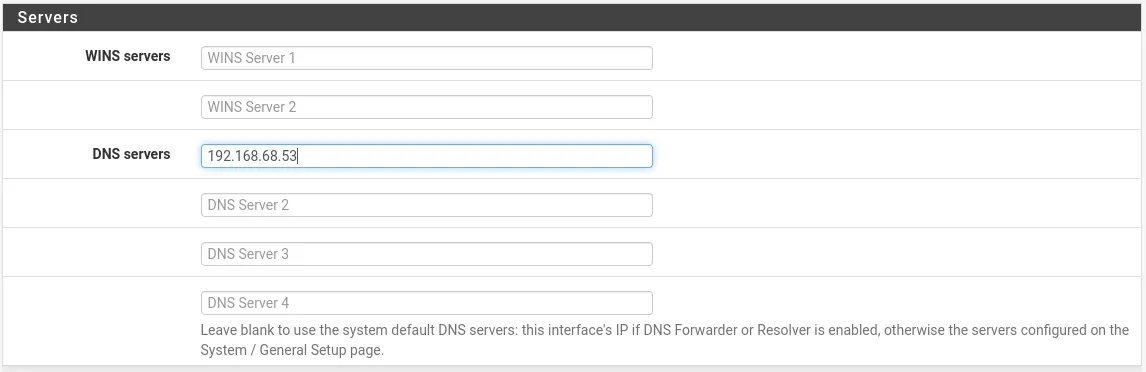
Set the Pi-Hole’s IP address (something like 192.168.68.53) as the only DNS server on your network. Make sure you zero out the other DNS servers.
With the newly set DNS server, you’re done setting up Pi-Hole. It will start to block ads everywhere for any device on your network. To tweak the Pi-Hole’s configuration, visit http://pi.hole on your network.
Updating Pi-Hole
- The first step in updating Pi-Hole is to access the machine’s console. Do this by using the machine’s physical keyboard or logging in using SSH:
ssh username@pi.hole
- Once inside, run the following command:
pihole -up
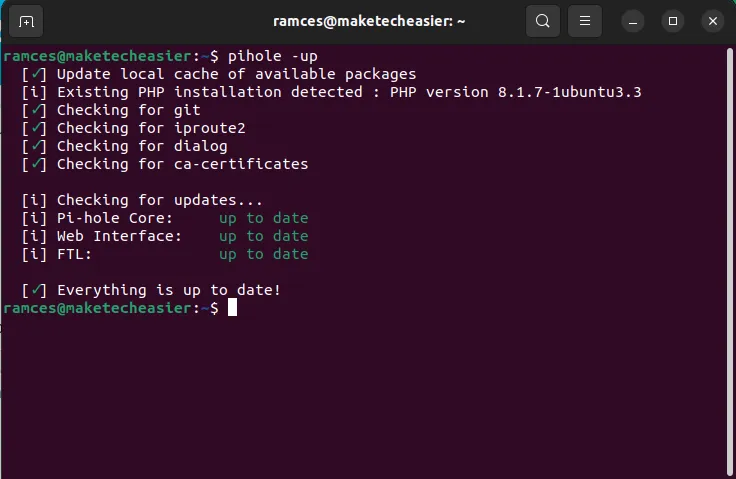
- Restart your machine to apply the new settings and binaries:
sudo reboot
Setting Up a Custom DHCP Server
Aside from acting as your network’s DNS server, Pi-Hole can also assign IP addresses to your machines using DHCP. This can be helpful in instances where you want to control how many new devices can use your network.
- Disable your router’s DHCP server. As it’s similar to setting up DNS, this step will vary depending on the router you have.
- Go to your Pi Hole’s web configuration page.
- Click the “Settings” category on the page’s left sidebar.
- Click the DHCP tab.
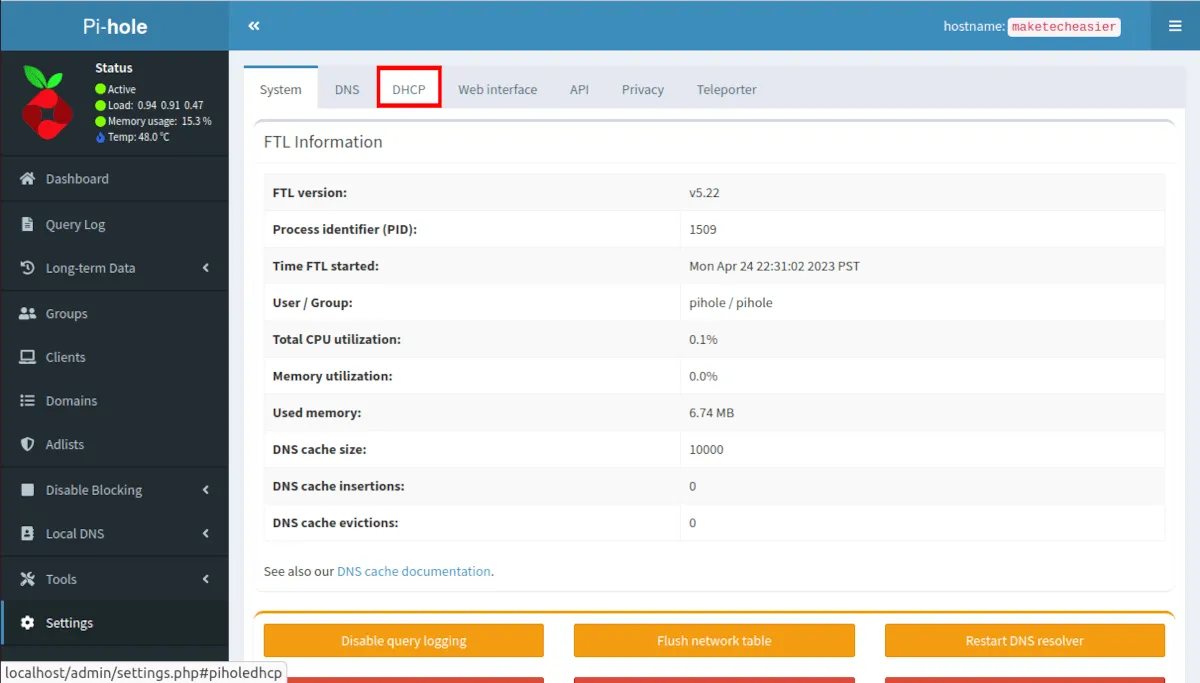
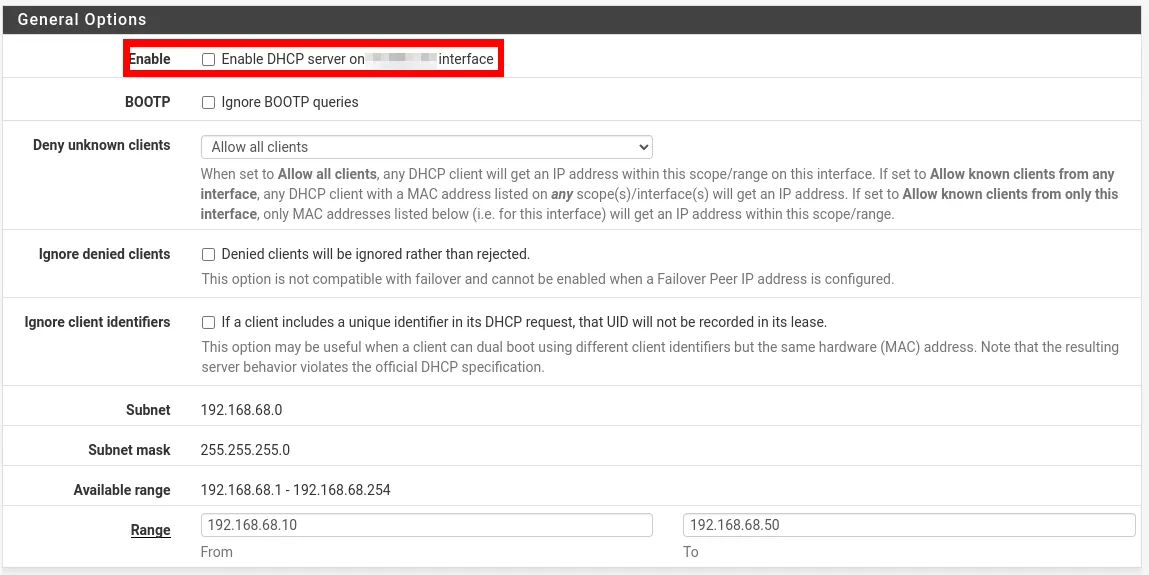
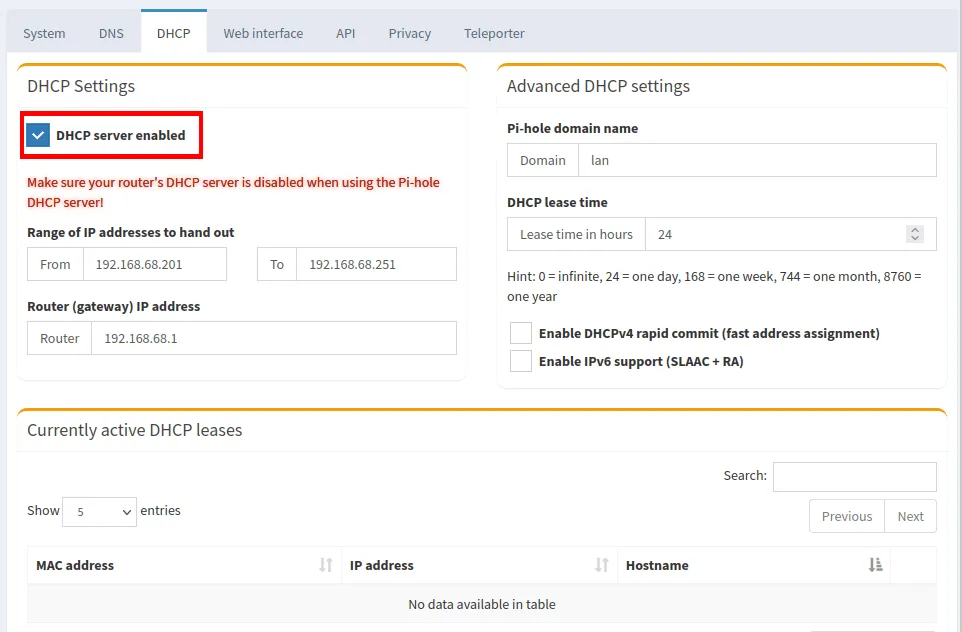
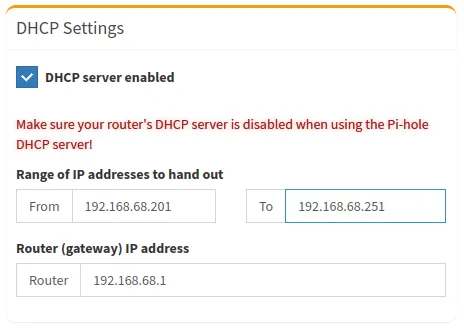
- Click the “DHCP server enabled” checkbox.
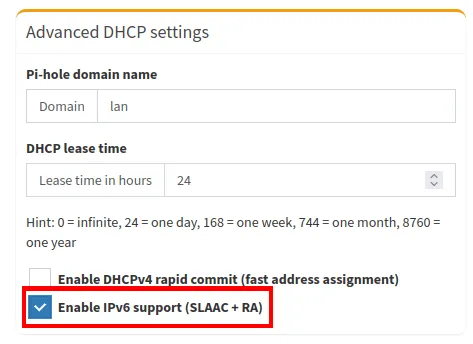
- Click “Enable IPv6 Support (SLAAC + RA)” to also allot IPv6 addresses to your local machines.
- Select the “To” textbox under the “Range of IP addresses to hand out” subcategory.
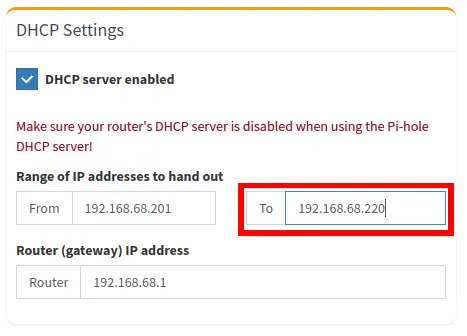
- Replace the content of the “To” textbox with the last IP address that you want DHCP to hand out. In my case, setting this value to “192.168.68.251” will limit the number of clients that can use my network to 50.
Creating a Custom Blocklist in Pi-Hole
Pi-Hole uses a central blocklist maintained by its developers. This approach means that the program can quickly include a new set of malicious domains as soon as they go online. You can also add your own domains in a custom blocklist.
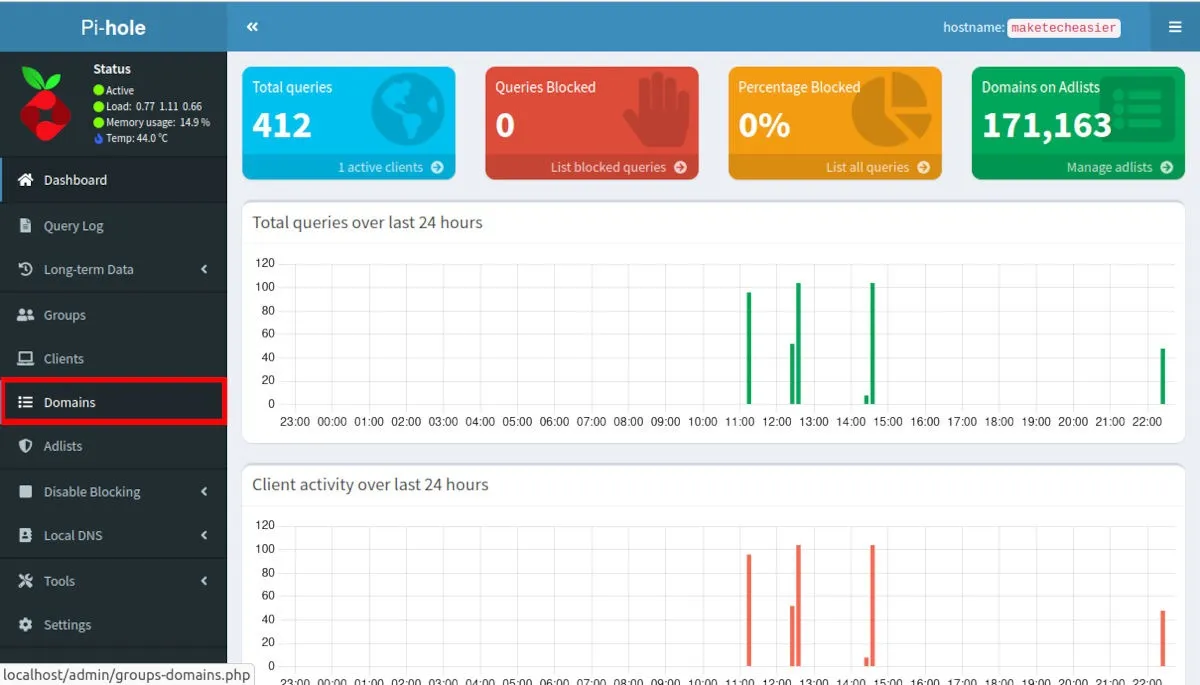
- Go to your Pi-Hole’s web configuration page.
- Click the “Domains” category on the page’s left sidebar.
- Select the “Domain” textbox and enter the domain that you want to block.
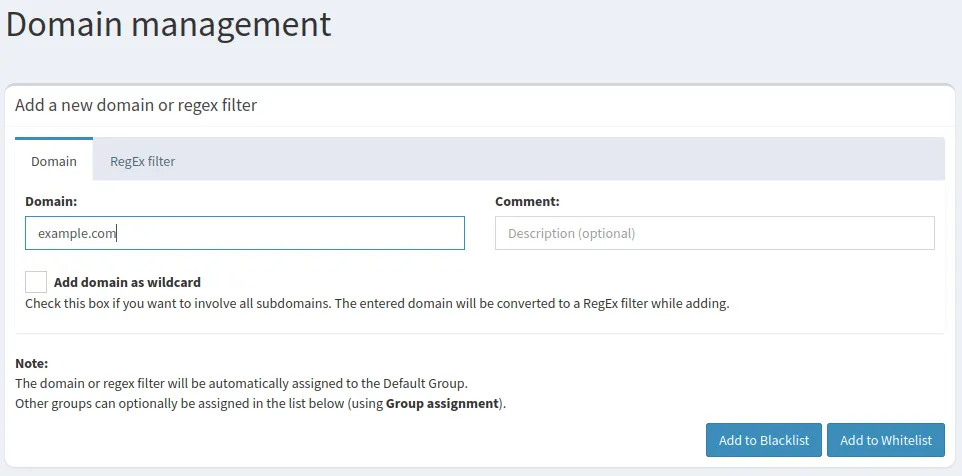
- Click the “Add to Blocklist” button.
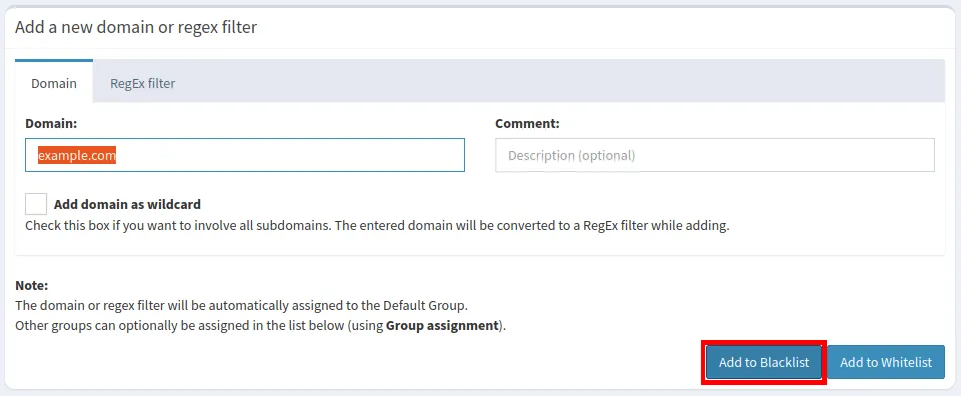
- While this will add the address to your machine’s internal blocklist, it will not include any subdomains and subdirectories present in the address. This can be an issue if you want to block an entire site from loading in your network. To fix this, click “RegEx filter” in the Domain subpage.
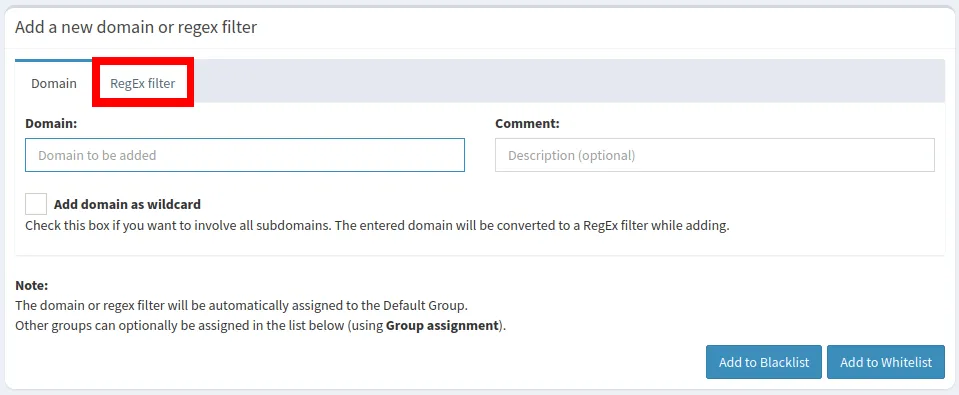
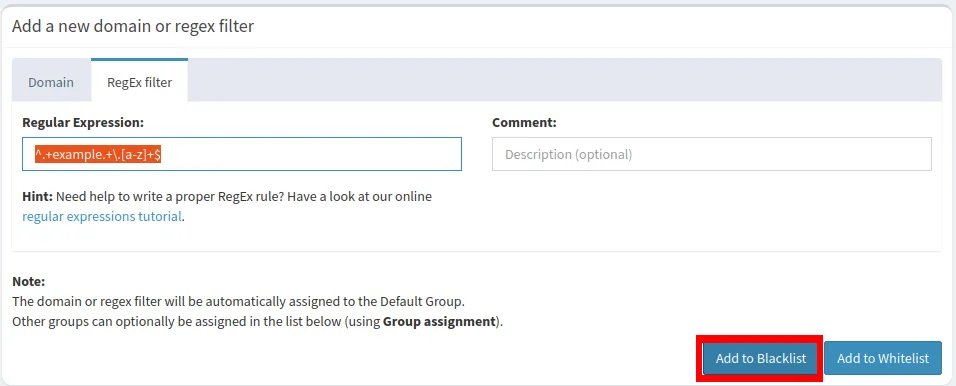
- Click the “Regular Expression” textbox.
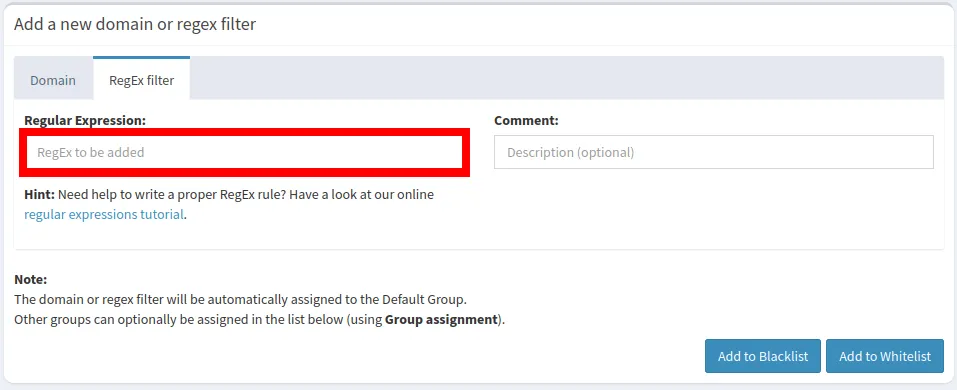
- Write your domain in a regular expression format. For example, the following line of text blocks all subdomains and variations of “example.com.”
^.+example.+\.[a-z]+$
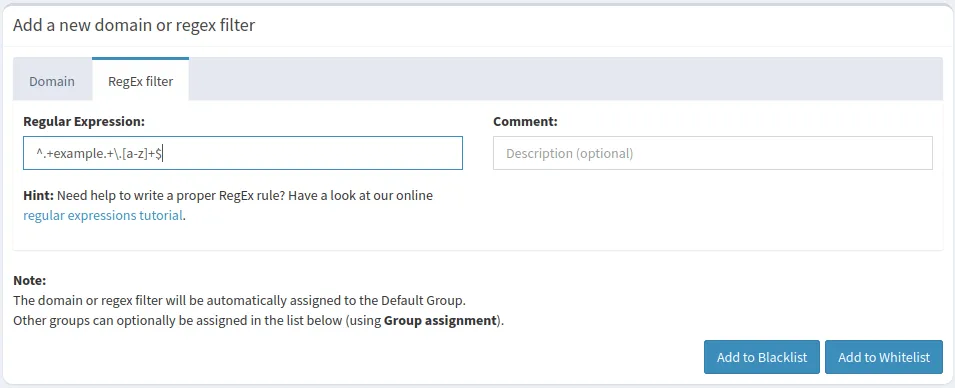
- Click “Add to Blocklist” to apply your custom list.
Frequently Asked Questions
Is it possible to reconfigure an existing Pi Hole installation?
Yes. Do this by logging in to your Pi-Hole’s machine console and running: pihole reconfigure. This will rerun the initial setup process and reinstall all of Pi-Hole’s packages, scripts and dependencies.
Is it possible to check on Pi-Hole without using a web browser?
While the developers of Pi-Hole designed it to work with a web browser, you can also use your console to print a simple overview screen. You can run a TUI screen for Pi-Hole by using the following command: pihole -c -e.
Is it possible to look up whether a domain is being blocked by Pi-Hole?
Yes. Do this by going inside your machine’s console and using the query subcommand. For example, running pihole -q -exact -all malicious.example.com will print all the blocklists that contain an instance of “malicious.example.com.”
Image credit: Unsplash. All alterations and screenshots by Ramces Red.
Leave a Reply