5 of the Best Steganography Tools in Linux

Steganography is the art and process of putting one type of information inside another in an attempt to hide it. This is often done in situations where an individual wants to preserve secret information inside normal objects.
This article will show 5 of the best of steganography tools currently available in Linux. Not only that, it will also show you how you can hide your first message using these utilities.
What is Steganography and Why Use It
Steganography is not a new innovation. Since the time of ancient Greeks, historians have written on how cultures used steganography to hide information in plain sight. To that end, one famous account was Herodotus’ story of Histiaeus where he tattooed a short message on a servant’s bare scalp.
Since then, advances in technology have allowed individuals to use steganography even inside digital objects. For example, it is now possible to insert an entire book inside a simple JPEG photograph.
One of the biggest advantages of using steganographic tools is that they are simple and easy to use. In most cases, these programs are just simple command line utilities that take your message and a dummy file.
Another advantage of steganographic tools is that you can get them for free. Most developers nowadays license their utilities as Free and Open Source Software (FOSS). As such, you only need to have a computer and an internet connection to get started with steganography.
1. Steghide
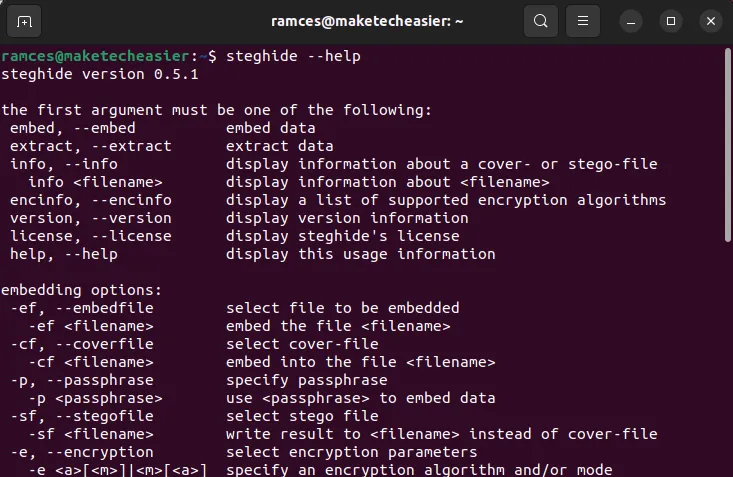
Steghide is one of the most popular steganographic tools today. It is a simple command line program that encodes text inside images. Steghide works by creating a random list of bits inside your dummy file and inserts your secret data in between those bits.
This approach means that your data will seamlessly blend in with your dummy file. Further, steghide also comes with solid compression and encryption algorithms by default. This ensures that it would be hard to extract your information even if a bad actor knows that your file contains secret data.
You can install steghide in Ubuntu and Debian by running the following command:
sudo apt install steghide
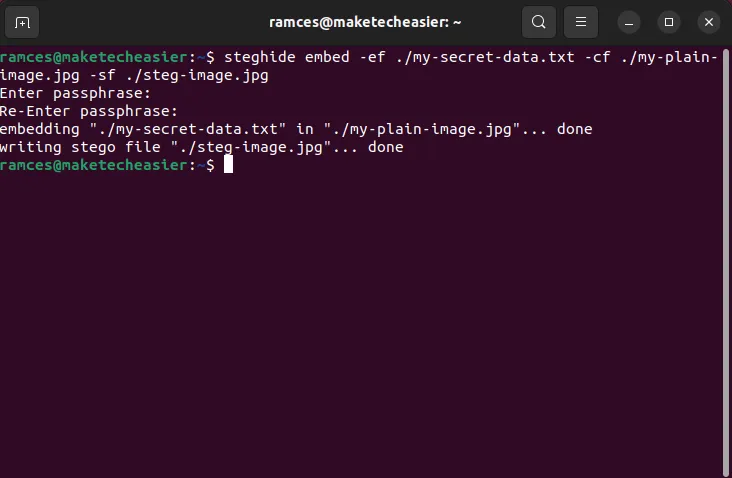
Once done, you can run this command to create your first steganographic file:
steghide embed -ef. /my-secret-data.txt -cf. /my-plain-image.jpg -sf. /steg-image.jpg
Pros
- Quick and easy to use
- Uses checksums to verify the integrity of data
Cons
- The output is noticeably larger than the original
- It modifies small bits of the original dummy file
2. Stegoshare
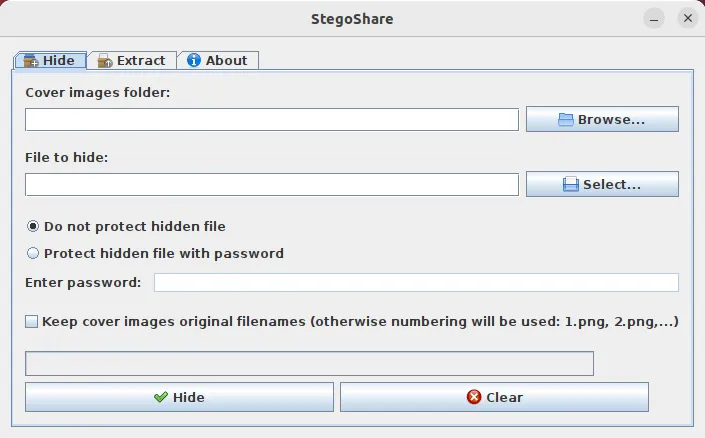
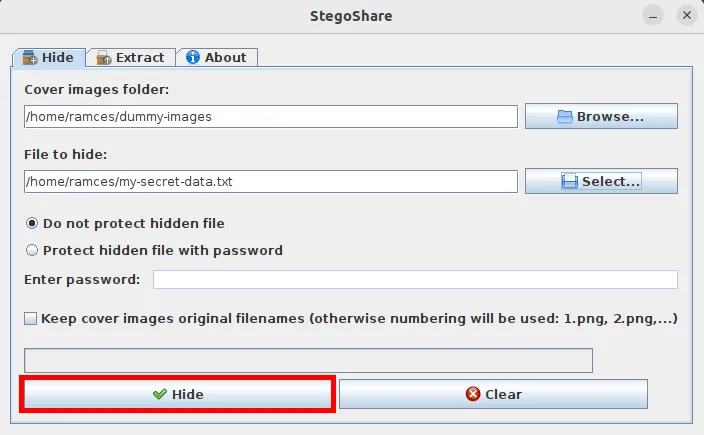
Stegoshare is a graphical steganographic tool that provides users with an intuitive interface for hiding data inside image files. Unlike steghide, stegoshare excels in allowing you to encode large binaries inside multiple files.
Another key advantage of stegoshare over other tools is that it is highly portable. This means that you can distribute the program to other users regardless of the OS that they are on. For example, you can encode in Linux and still decode it on Windows.
- To use stegoshare, you need to first install its dependencies:
sudo apt install wget openjdk-8-jdk openjdk-8-jre
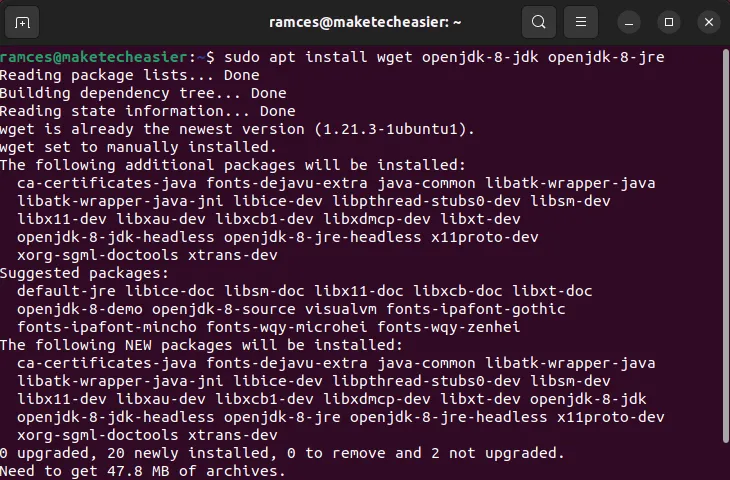
- Download stegoshare’s binaries from the developer’s website:
wget http://downloads.sourceforge.net/stegoshare/StegoShare.jar
- Run the program and click “Browse.”
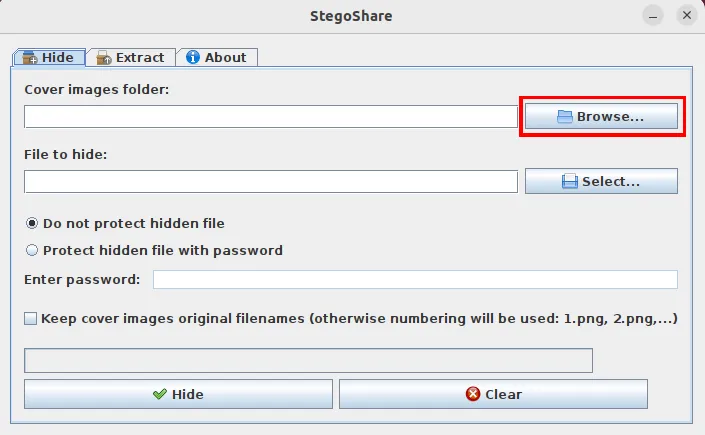
- Select your dummy image folder.
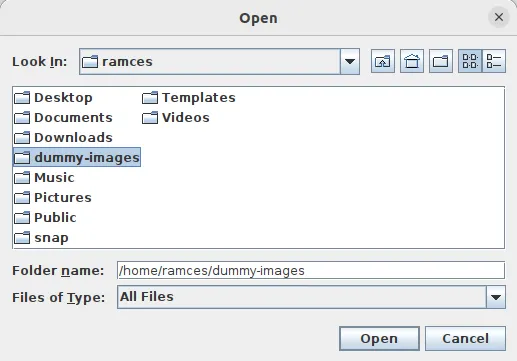
- Click the “Select” button underneath “Browse.”
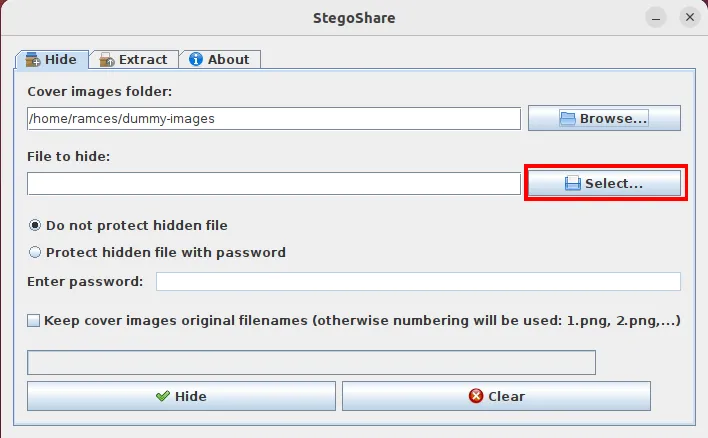
- Select the file that you want to hide.
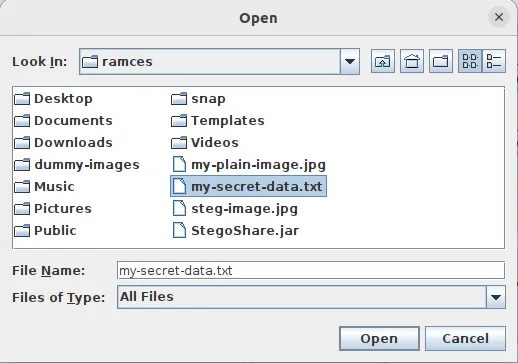
- Click the “Hide” button to encode your secret data to your dummy file.
Pros
- It is simple and easy to use
- It works on any platform that runs Java
Cons
- It produces large files
- Image analysis tools can detect stegoshare’s algorithm
3. Wavsteg
Aside from embedding information inside images, you can also hide your information using sound files. Wavsteg is a simple, yet effective tool that allows you to blend secret data in between the bits of a digital audio file.
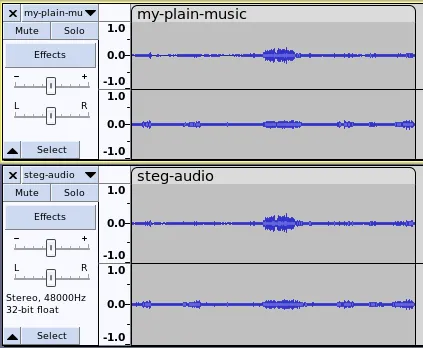
wWavsteg reads an entire audio file and looks for its “Least Significant Bits.” These are the parts of a file that neither delete nor modify the data inside it. This means that an audio file that contains secret data will not have any audible difference from a “clean” file.
- Install its dependencies:
sudo apt install python3 python3-pip
PATH=$PATH:/home/$USER/.local/bin/
- Install the program using pip:
pip install stego-lsb
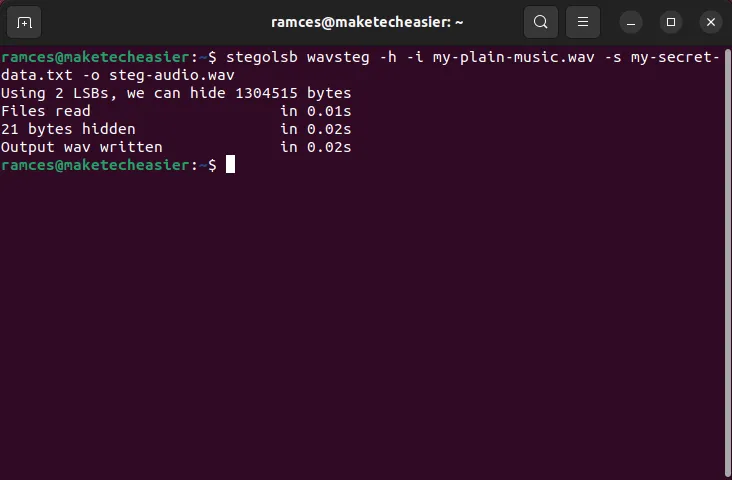
- Once installed, you can start to encode data inside your audio files with the following command:
stegolsb wavsteg -h -i my-plain-music.wav -s my-secret-data.txt -o steg-audio.wav
Pros
- It is lightweight and simple to use
- No audible difference between other audio files
Cons
- It only works with text files
- It can produce large files
4. Snow
Snow is a lightweight tool that uses whitespace and tabs to hide information inside text files. This means that, unlike other steganographic tools, snow does not rely on binary formats to encode secret data. This can be incredibly useful in cases where it is not possible to share large binary files.
Since snow only relies on plain text, it is still possible to compress and encrypt your files similar to a binary file. As such, snow can produce extremely small files that can blend in with other text data.
- You can install snow with the following command:
sudo apt install stegsnow
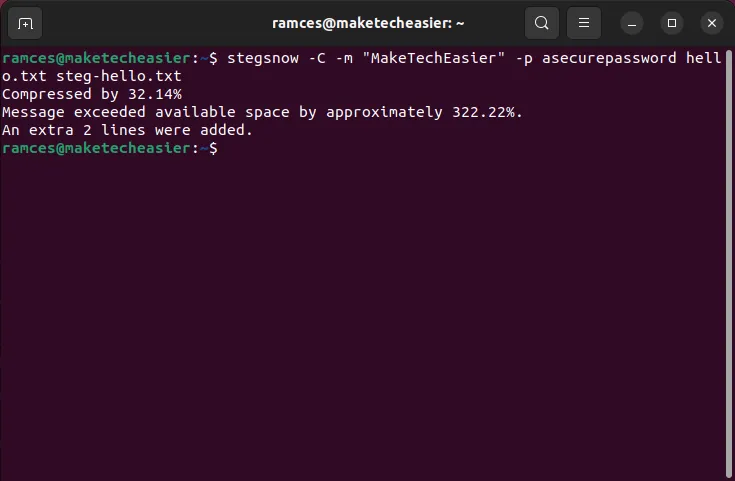
- Use the following command to hide the phrase “MakeTechEasier” inside the file “hello.txt.”
stegsnow -C -m "MakeTechEasier"-p asecurepassword hello.txt steg-hello.txt
Pros
- It produces small files
- You can use its output text on any program that accepts plain text
Cons
- Data space can be extremely limited
- Its encryption algorithm is relatively outdated
5. Steganoroute
Digital steganography traditionally conceal information within a file. However, it is also possible to use steganography without using dummy files.
Steganoroute is an innovative networking tool that allows you to hide information using TCP. The way it works is that the program creates fake ICMP packets that contain the message that you want to send. A host can, then, listen to the server for its fake packets and decode its information using a network analysis tool.
- Install steganoroute’s dependencies:
sudo apt install git mtr python3 python-scapy
- Clone the program source code from its repository:
git clone https://github.com/stratosphereips/steganoroute.git
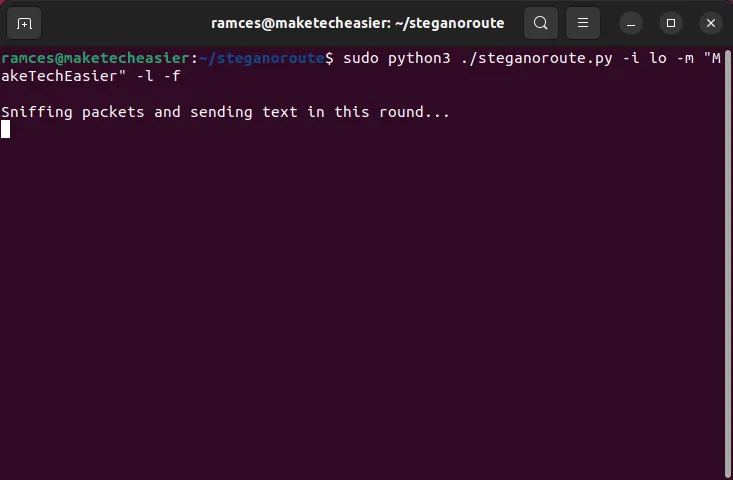
- You can broadcast your steganoroute messages by running the following command:
cd. /steganoroute
sudo iptables -I INPUT -p icmp --icmp-type 8 -j DROP
sudo python3. /steganoroute.py -i lo -m "MakeTechEasier"-l
- Test if the program is broadcasting properly by using the
mtranalysis tool:
mtr -t your.local.lan.ip
Once it is running, you also need to press D to print the message.
Pros
- It does not depend on creating dummy files
- You only need to broadcast to share messages
Cons
- It relies on forging ICMP packets
- Malicious actors can intercept the packets and reconstruct your message
Frequently Asked Questions
Will steganography change how my file behaves?
No. By default, steganographic tools aim to retain as much of the original data as possible. This means that you can share your file to others and they would still be able to use and access the original file.
I sent a steganographic picture and it lost its message.
This is most likely due to an issue with your image hosting provider. Most image sharing website today tend to compress images as soon as it hits their servers. This is a problem for steganographic tools because they on the exact data structure of the original image file.
As such, make sure that your image hosting provider is not compressing any images that you send on their server.
Are there any downsides to hiding data using steganography?
It depends. For the most part, tools such as steghide relies on hiding data inside regular digital files. While steganography will not change how a file behaves, it will still leave a noticeable imprint on a digital file. This can be a problem if a malicious actor is aware that you are using steganography.
My steganoroute recipient is not receiving my ICMP packets.
This is most likely due to your steganoroute server sending its ICMP packets at the wrong interface. To fix this, find the networking interface that you want to use using ip addr.
After that, add the -i option followed by your networking interface. For example, the following runs steganoroute through my ethernet port: sudo. /steganoroute.py -i enp3s0 -m "MakeTechEasier"-l.
Image credit: Icons8 Team via Unsplash. All alterations and screenshots by Ramces Red.
- Tweet


Leave a Reply